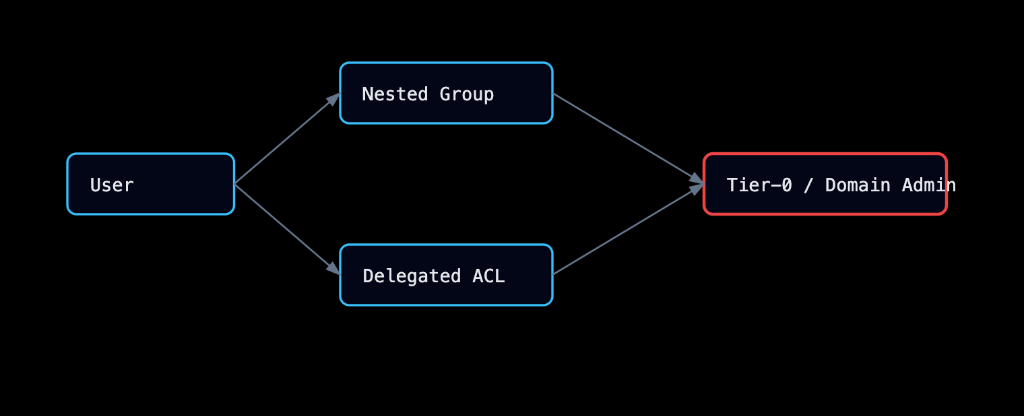
TIER-0 ATTACK PATH PREVENTION.
STOP REACTING. START CLOSING GAPS.
Proactively eliminate hidden privilege escalation paths in Active Directory and Entra ID before ransomware chains them together.
🔒 100% Read-Only & Non-Intrusive. No agents required.
“Modern ransomware doesn’t break in—it logs in, escalates quietly, and takes Tier-0 without triggering alerts.”